I. INTRODUCTION
In recent years, the car-sharing platforms emerging as popular and sustainable transportation alternatives. However, traditional authentication methods, such as passwords or physical keys, have proven susceptible to various security risks. For example, they make it impossible to confirm the physical presence of a certified driver in the car and offer limited user control over personal data. Consequently, the identity fraud in a car-sharing environment is a real problem [1]. On the other hand, verifying user identity is a complex issue, not only in car-sharing environments but also in various other contexts. The advancement of biometric technology has facilitated its wide applications in law enforcement, border control, healthcare, and financial identification and verification. Due to the peculiarity of biometric features, such as their immutability, permanence, and uniqueness, ensuring security and privacy is crucial to maintaining integrity, reliability, and availability in biometric-related applications [2]. These contexts all require reliable and secure user verification methods.
Biometric authentication, which relies on unique physiological or behavioral characteristics, offers a more secure and convenient alternative. The uniqueness of biometric identifiers is intrinsically tied to an individual's identity and is distinct for every person. If biometric data are compromised in one system, all other systems relying on the same biometric information are at risk. This could potentially lead to widespread identity theft and significant data security breaches. Hence, despite the advantages offered by biometric systems, this is one of the significant vulnerabilities [2]. Additionally, the European Data Protection Supervisor has noted that centralized databases, as opposed to decentralized ones, inherently raise the risk of misuse. Such central storage systems also tend to attract intentions to repurpose the data for ends not originally intended, thus posing challenges to privacy preservation [3].
To address the above issues, we propose a decentralized framework for ensuring privacy in a biometric identity verification system. The development of a decentralized biometric authentication system would significantly improve the authentication landscape in car-sharing applications. This system aims to foster trust, enhance user experience, and promote the adoption of sustainable and reliable transportation solutions compared to traditional authentication methods, such as Know Your Customer (KYC) systems. KYC processes heavily rely on identity management, and current systems vary from service to service, requiring users to provide personal data and complete the KYC procedure each time they register with a new service. This makes current KYC systems time-consuming, increases the risk of data breaches, lacks a unified or standard solution, and is expensive for companies that must use different services.
In our system, we use blockchain technology in supporting multi-party processes where members do not trust each other [4-5]. Blockchain technology stands as a decentralized and tamper-proof ledger system, which came to prominence with the advent of Bitcoin in 2009 [6]. It answered a longstanding question within the cryptographic community on achieving consensus on financial transactions in a distributed manner without central oversight. Biometric technology, in contrast, focuses on verifying identities using unique physical (like facial features or fingerprints) or behavioral (such as voice patterns or handwriting) characteristics. The fusion of biometrics with blockchain could significantly enhance distributed digital identity systems built upon blockchain technology, introducing a plethora of new applications. For instance, biometrics could refine the authentication processes for smart devices — objects that interact with blockchains to perform actions or make decisions based on the recorded data. A practical example is a vehicle that can be rented or purchased via a smart contract on a blockchain, where the challenge remains to effectively identify the user for such transactions [7].
However, while blockchain provides excellent architecture and practical tools for securing and managing sensitive and private data stored in biometric templates, several limitations exist. These include low transaction processing capacity (around tens of transactions per second), the need to store all system transactions, leading to rapid growth in the required storage space, and insufficiently studied robustness against different types of attacks. Additional limitations encompass the economic cost of executing smart contracts, privacy concerns, and challenges related to scalability and processing capability [7].
To address these issues, we propose a user-centric and privacy-preserving authentication framework that leverages SSI, DIDs, off-chain storage, and Homomorphic encryption. Combining blockchain and biometrics could be beneficial for novel applications in biometrics, such as the PKI mechanism, distributed trusted service, and identity management. It is argued that while blockchain provides immutability, accountability, audibility, and availability to biometric solutions, biometrics can augment blockchain by offering a secure digital identity model to access digital assets or introducing biometric wallets. Creating a digital identity on blockchain enables individuals to control who and how to access their personal information easily. During past years, identity management has been the second most popular topic for blockchain and biometrics integration [3]. In summary, the primary objectives of this research are:
-
Investigating the existing authentication methods in car-sharing platforms and identifying their limitations concerning privacy, security, and user control.
-
Exploring the potential of decentralized identity management systems, specifically DIDs, in enhancing privacy and security in biometric authentication.
-
Examining the role of off-chain storage solutions and Homomorphic Encryption in protecting user privacy and ensuring secure identity verification.
-
Designing a decentralized biometric authentication system that addresses the identified limitations and incorporates user-centric identity management, GDPR-compliant data handling, and artificial intelligence (AI)-driven biometric verification.
This paper is organized as follows: Section 2 discusses the technologies used in this approach and the legal aspects. Section 3 introduces our system and its algorithms. Section 4 covers the implementation and evaluation, including simulation results for better understanding. Finally, Section 5 concludes this paper.
II. PRELIMINARY
In the real world, we rely on governments to issue identity credentials in the form of physical representations such as passports, birth certificates, and driver's licenses. These documents contain information that is kept by a central authority, usually in protected digital storage. However, we use physical copies of these documents independently of those centralized systems for identification purposes because of their convenience and portability. For example, we can open a bank account or travel on an airline by using only our driver's license as it represents a verified set of data about us [8]. However, in a digital world, people tend to use KYC systems to identify themselves. Customer identification, authentication, and verification form the foundation of KYC procedures, which are essential for many businesses, including banking, telecommunications, and shared services like car rentals [9]. The KYC process is designed to prevent identity theft, financial fraud, money laundering and terrorist financing.
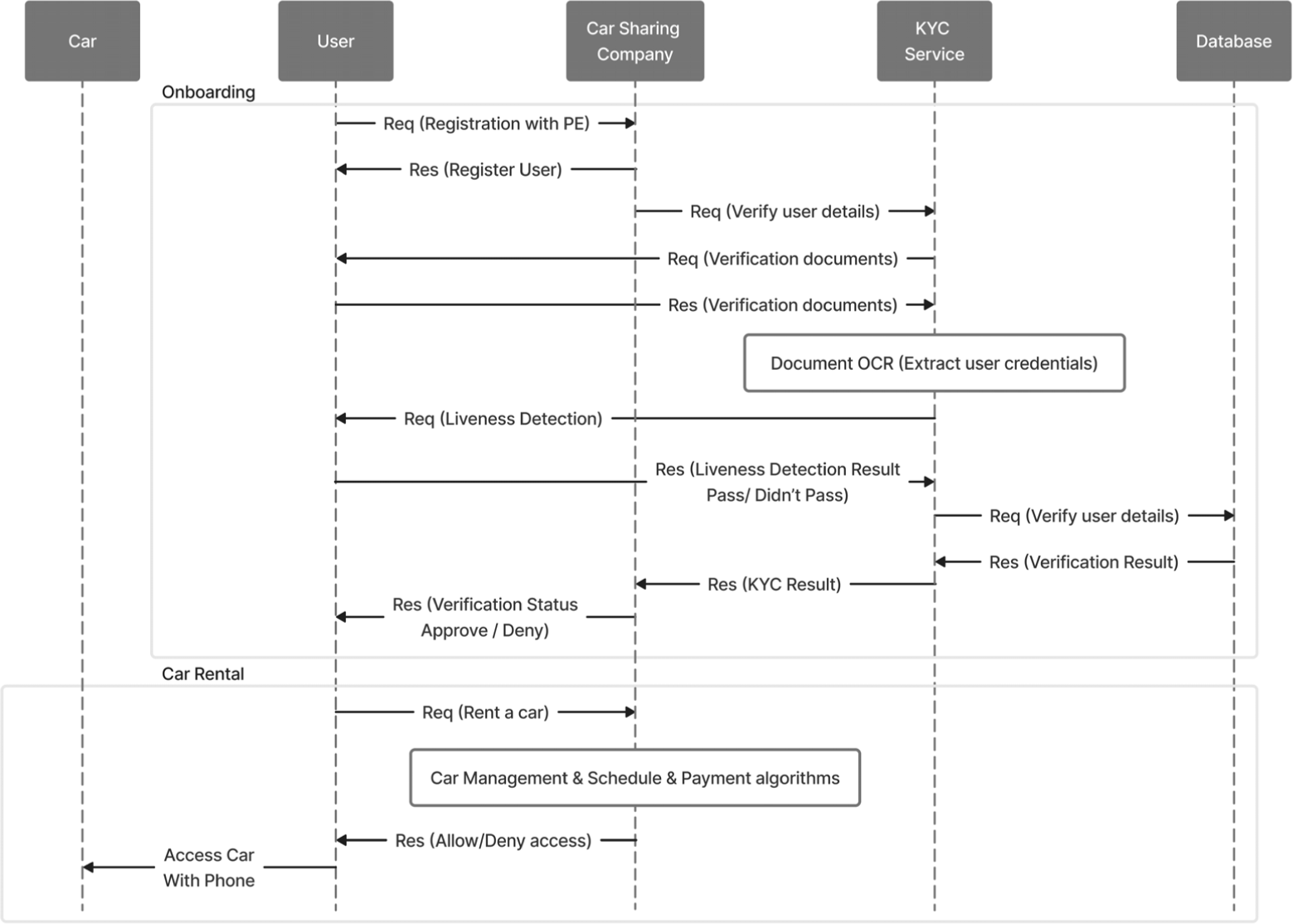
However, existing KYC processes are often seen as intrusive, time-consuming, and prone to errors. A major concern is that they typically require customers to share sensitive personal information, posing privacy risks. Additionally, traditional KYC procedures are often manual, which can lead to human errors and inefficiencies [10]. An innovative area where efficient and reliable KYC procedures are critical is in the field of contactless car-sharing applications. These applications allow users to rent cars for short periods, often by the minute. The process is entirely app-based, with users locating, unlocking, and starting cars directly from the app [11]. To ensure secure transactions and prevent unauthorized usage, car-sharing services must implement robust KYC procedures. When a user signs up, they provide their personal details and driver's license information. The system then verifies this information against various databases to ensure its accuracy and validity. Fig. 1 shows the sequence diagram of the current contactless car-sharing system.
Current authentication systems used in contactless car-sharing environments typically authenticate users during enrollment. Mobile app authentication requires users to authenticate themselves through a dedicated car-sharing mobile app, which communicates with the vehicle to unlock the doors and start the engine. However, after a user is enrolled and has booked a car, such applications do not verify the driver's identity, and they have no ability to do so. This can lead to identity fraud, as the car may be booked by a certified driver, but the actual driver may not have a valid driver's license.
In a digital era, the management of digital identities has become a critical issue. Traditional centralized identity systems pose significant privacy and security concerns, resulting in a growing interest in decentralized identity management systems. SSI, DID, and VC are innovative technologies that could revolutionize the way we manage and verify identities in the digital world. SSI is a concept that allows individuals or organizations to have complete control over their digital identities [12]. Unlike traditional identity systems, where identities are managed by a central authority, in an SSI model, individuals hold their identities and control how their personal information is shared and used. A crucial element of SSI is the DID, a type of identifier that is self-created, globally unique, and not reliant on any centralized registry, identity provider, or certificate authority [13]. DIDs are stored on a decentralized network, such as a blockchain, and can be resolved to DID documents that contain public key material, authentication descriptors, and service endpoints, enabling secure, privacy-preserving communication and interaction. VCs, on the other hand, are digital equivalents of physical credentials, such as driver's licenses, passports, or university degrees [14]. They are tamper-evident and cryptographically verifiable, meaning they can be trusted to be genuine and not manipulated. The issuer of a VC can be independently verified, and the holder of the VC can prove they are the legitimate owner without exposing the actual data contained in the credential.
These technologies can provide significant benefits. They offer enhanced privacy, as users can control who accesses their data and for what purpose. They improve security by eliminating the need for centralized databases that can be targeted by hackers. One potential application of these technologies is in KYC processes. An individual could hold a VC that proves their identity, issued by a trusted authority. When they need to prove their identity, they present the VC, which can be cryptographically verified by the relying party. The individual doesn't need to provide any additional personal data, and the relying party doesn't need to conduct any further checks. This could streamline KYC processes, reduce privacy risks, and provide a better user experience.
Fig. 2 shows the traditional DID scheme. This structure benefits the biometric system by allowing full control of identifiers of the subject with an individual biometric identifier, independent of different heterogeneous providers. Thus, biometrics could significantly improve currently distributed digital identity schemes based on the blockchain. In terms of on-chain challenges, DIDs help transfer most of the processing load from the main blockchain to the off-chain network. A DID document consists of three fundamental parts: an authentication key, an authentication method, and a service endpoint. Whoever has access to the key is entitled to access the DID document. Therefore, we suggest future research use biometric data only in combination with similar specifications, i.e., off-chain, minimizing both the quantity and sensitivity of personal data stored on-chain.
Blockchain technology, initially conceived for the cryptocurrency Bitcoin, has been recognized for its potential to transform various industries [15]. A blockchain is a distributed ledger that allows multiple parties to reach a consensus on a single version of shared digital history. Its immutable nature and transparency make it a highly reliable system for many applications, including authentication and verification [16]. In the context of digital identity, blockchain can be used to store DIDs and their associated public keys securely. This allows individuals to prove their identity without revealing any personal data, enhancing privacy and security. Furthermore, the cryptographic nature of the blockchain ensures the integrity of the DIDs, making it nearly impossible for identities to be forged or altered.
Moreover, blockchain and smart contracts can be used to verify transactions and interactions. For example, in a blockchain-based voting system, a smart contract could automatically verify each vote's validity, ensuring that only eligible voters can vote and that each voter can only vote once [17]. This can significantly increase the transparency and integrity of the voting process, strengthening trust in the system.
In the realm of decentralized data storage and management, a critical evaluation of cost-effectiveness and efficiency is paramount. The choice between utilizing blockchain (or smart contracts) and alternative storage solutions such as the IPFS (InterPlanetary File System) hinges significantly on the associated costs [18]. Analyzing the cost implications, it is observed that storing 1 kB of data via a smart contract execution on the Ethereum blockchain consumes approximately 2,155,120 gas. Given the Ethereum price of 1,574.26 USD as of October 18, 2023, the resultant cost equates to around 47 USD per 1 kB of data. In a practical application where encrypted biometric features approximating 446 kB need to be stored, the financial expenditure escalates to an approximate value of 20,962 USD. Additionally, the storage of a public key, which typically encompasses substantial data, in this case around 47.3 MB, further inflates the cost to an estimated 2,223,100 USD.
Considering such substantial costs, even the exploration of alternative networks does not present a viable economic solution due to the inherently high expenses associated with substantial data storage on blockchain technologies. Thus, an optimized approach involves leveraging IPFS for the storage of substantial content such as encrypted biometric features and public keys. Concurrently, the blockchain can be utilized efficiently by storing only the DID URI linked with the Content Identifier (CID). This strategic approach significantly reduces the data storage requirements on the blockchain to an estimated 100 kB, thereby reducing the execution cost to about 451,325 gas. Based on the pricing as of October 18, 2023, this translates to a cost of approximately 9.9572 USD, representing a pragmatic and cost-efficient strategy for decentralized data storage and management. Consequently, by implementing IPFS and blockchain, we still ensure that there is no single point of failure, and since only encrypted versions of biometrics are stored online, privacy is preserved.
Homomorphic encryption is a transformative cryptographic technique that facilitates computations on encrypted data without necessitating its decryption. This ensures that sensitive data remains confidential throughout computational processes, thereby bolstering its security and privacy. The concept remained largely theoretical until 2009, when Craig Gentry presented the first fully homomorphic encryption (FHE) scheme [19]. This FHE scheme utilized lattice-based cryptography and allowed both addition and multiplication on encrypted data. The significance of homomorphic encryption lies in its potential applications, especially in cloud computing. It enables data owners to outsource computations to cloud servers without compromising the confidentiality of their data. Since Gentry's pioneering work, there has been a surge in research dedicated to optimizing and enhancing the efficiency of homomorphic encryption schemes. Notable advancements include leveled homomorphic encryption, which allows users to set a limit on the depth of computations [20], and bootstrapping techniques that refresh ciphertexts to reduce noise [21]. These innovations are paving the way for the practical implementation of homomorphic encryption in real-world scenarios, such as secure voting systems, private medical data analysis, and encrypted search.
In practical application scenarios like neural networks, the introduction of hierarchical Galois keys proves to be highly efficient. For example, with the use of the proposed hierarchical Galois keys, the implementation of networks such as ResNet-20 and ResNet-18 becomes more feasible, as evidenced by the reduced memory requirements and the maintenance of competitive classification accuracies in encrypted domains. Furthermore, homomorphic encryption, leveraging the innovative use of Galois keys and other optimizations, finds substantial applications in supply chain security, regulatory compliance, and private data analytics. This cryptographic method enables secure third-party computations, adherence to rigorous data protection regulations such as the GDPR, and private and secure data analytics operations.
Galois automorphisms are intrinsic to field theory in mathematics, with profound applications in homomorphic encryption, particularly in schemes like the Brakerski-Fan-Vercauteren (BFV) and Cheon-Kim-Kim-Song (CKKS). A Galois automorphism is defined as an isomorphism from a field to itself that preserves field operations, mathematically represented as
for all (a,b) in a field (F), where (\sigma: F to F) is a bijective map.
In the context of HE, Galois automorphisms facilitate essential operations such as rotation and permutation on encrypted data, enhancing the utility of encryption schemes for complex operations without decryption. This is pivotal in algorithms related to AI and machine learning (ML), where encrypted data can be manipulated efficiently, preserving privacy and security.
Schroff et al. [22] introduced FaceNet, a remarkable system proficient at directly learning a mapping from face images to a compact Euclidean space where distances authentically signify face similarity. In this well-constructed space, conventional tasks like face recognition, verification, and clustering become straightforward, utilizing FaceNet embeddings as pivotal feature vectors. Employing a deep convolutional network, this methodology is distinct, optimizing the embedding directly and bypassing the intermediate bottleneck layer optimization common in previous deep learning strategies. A unique online triplet mining method is used for training, employing triplets of nearly aligned matching/non-matching face patches. This innovative approach enhances representational efficiency, enabling exemplary face recognition performance while requiring only 128 bytes per face.
The FaceNet model architecture, as depicted in Fig. 3(a), encompasses a batch input layer and a profound CNN, succeeded by L2 normalization, culminating in the generation of face embeddings. The influential triplet loss is applied during the training phase.
Triplet Loss plays a crucial role in diminishing the distance between an anchor and a positive (of identical identity) while concurrently maximizing the distance with a negative from a different identity. The process is shown in Fig. 3(b). Triplet Loss, essential for optimization during training, is computed using the equation:
where:
The squared L2 distance metric is crucial in measuring similarities between embeddings. This metric computes the square of the Euclidean distance between two points in the embedding space, ensuring effective differentiation between various face embeddings.
Here, D(x,y) symbolizes the squared L2 distance between the embeddings of images (x) and (y).
III. PROPOSED SYSTEM
In this section, we present a pioneering decentralized biometric authentication system designed for car-sharing services, integrating DID, off-chain data storage solutions, and AI to enhance the accuracy of biometric verification. Our system incorporates FHE and leverages the IPFS for secure and efficient data handling, thereby allowing temporary biometric verification access while guaranteeing the privacy and security of user data. By storing encrypted biometric data off-chain, we significantly mitigate privacy risks. The FaceNet model is utilized to refine the verification process, ensuring a smooth and efficient user experience. Our approach to secure identity verification within the car-sharing context aims to instill a higher degree of trust among stakeholders in the ecosystem.
Our framework is designed with a focus on user-centric identity management, compliance with GDPR through off-chain data storage, and the application of AI to streamline biometric verification processes. Users initiate their interaction with our system through an enrollment process, during which they create a DID, and the DMV issues a VC that is securely stored on the user's device. To rent a car, users present their digital driver's license, authenticated by the DMV. Biometric features are encrypted on the user's device using Homomorphic Encryption and subsequently stored on IPFS. The corresponding content identifier (CID) is linked to the user's DID URI, ensuring that once the authority verifies the biometric data, it cannot be altered. With the encryption keys held solely by the user, the privacy of the biometric information is preserved, as only the user has the capability to decrypt the data.
During the verification process, users authenticate themselves using in-car biometric sensors. The car-sharing service retrieves the encrypted biometric features from IPFS and computes the Euclidean distance between these and the features extracted during the rental process. Based on this encrypted comparison, the system determines whether to grant access to the vehicle. This innovative method enhances the security and privacy of the car-sharing service while maintaining a user-friendly interface. The detailed framework can be seen in Fig. 4.

The onboarding process consists of two phases: registration and verification.
Initially, government entities participating in our system, such as the DMV, must also register, enabling them to issue VCs subsequently. During user registration, the user creates an account within the DKMS application and generates their DID, which includes a DID URI, public key DID_Pk, and secret key DID_Sk. The DKMS then publishes the DID_Pk and DID_URI on the blockchain. Subsequently, the user captures a biometric image using their phone, and the DKMS application extracts features employing the method described in Algorithm 1 (see Section IV). The system then generates homomorphic encryption keys HE_Sk and HE_Pk, following the procedures outlined in Algorithms 2 and 3. The biometric features are encrypted with the HE_Sk like shown in Algorithm 4, and the encrypted data, along with the HE_Pk, is stored on IPFS. The user receives a CID that references the storage location, allowing other system participants to access the data. At this juncture, the registration phase concludes. However, the government must still manually verify that the biometric data belongs to the registering user.
For verification, the user visits a government institution and captures a biometric image on a designated device. This device extracts features using the same algorithm as before (Algorithm 1). The user then encrypts the extracted features with their HE_Sk. The DMV accesses the encrypted biometric data and the user's HE_Pk from IPFS. It computes the Euclidean distance over the encrypted data and sends the encrypted result back to the user's phone. Only the user can decrypt this result with their HE_Sk, and the user returns only the decrypted result to the DMV. Once verified, the DMV issues the digital driver's license (VC) to the user and records it on the blockchain. Despite its complexity, this verification process ensures security and is typically a one-time procedure.
The car rental process is streamlined compared to traditional methods. By enhancing the security of the onboarding process, reliance on additional KYC services is eliminated, as falsifying a digital license becomes infeasible. Car-sharing companies can verify users by accessing records on the blockchain. Thus, while the basic car rental process remains unchanged, the verification component is simplified. Users apply for a rental through the car-sharing app, presenting their digital driver's license. The car-sharing company verifies the VC_Pk against the blockchain and approves or denies the user's application. Other processes such as booking and payment, are outside the scope of this thesis and remain unchanged.
The user, upon entering the rented vehicle, captures their biometric image using the in-car camera. The vehicle extracts features using the prescribed method (Algorithm 1) and encrypts them with the user's HE_Sk. These encrypted features are sent to the car-sharing company, which then retrieves the previously stored encrypted features from IPFS to compute the Euclidean distance as outlined in Algorithm 8. The car-sharing company sends the encrypted result back to the vehicle, where the user decrypts it with their HE_Sk, enabling the car to decide whether to grant engine access. This crucial phase of the authentication process is delineated in Algorithm 10.
IV. IMPLEMENTATION AND EVALUATION
The evaluation of the system's performance was conducted on a computational setup possessing the following specifications:
The assessment entailed a comparative analysis of 280 unlabeled images, during which True Positives, False Positives, True Negatives, and False Negatives were meticulously determined through manual inspection. Moreover, the temporal duration required to execute each function for the respective pair of images was meticulously documented and stored in a tabular format. On the other hand, our experiment focused on evaluating the cost-effectiveness and efficiency of decentralized data storage solutions, particularly for the storage of encrypted biometric data and public keys. Given the high costs associated with storing large amounts of data directly on the Ethereum blockchain, we desire a hybrid approach using the Ethereum testnet and IPFS. We leveraged the Ethereum testnet to store DID URIs securely. Ethereum's testnet was chosen for its compatibility with smart contracts, allowing us to manage DIDs efficiently while leveraging the blockchain's security and decentralization features. Simultaneously, we employed IPFS for storing the actual data, including encrypted biometric features and public keys. IPFS was selected due to its cost-effectiveness for storing large files compared to direct storage on the blockchain. It provides a decentralized storage solution without a single point of failure, maintaining privacy by storing only encrypted data.
After importing images to compare, we extract features from them with DeepFace library [23]. The 'represent' function from the DeepFace library was utilized to derive vectorial representations, known as embeddings, of the facial images. The output of Algorithm 1, delineated in Fig. 5, elucidates the facial coordinates within the image and subsequently procures the feature sets as an array.
Algorithm 2 delineates the procedure for initializing the cryptographic context requisite for the generation of secret and public keys.

|
-
A cryptographic context for homomorphic encryption is initialized using the tenseal library.
-
ts SCHEME TYPE CKKS specifies the use of the CKKS scheme, which allows computations on encrypted real or complex numbers.
-
Parameters such as poly modulus degree and coeff mod bit sizes are specified for the encryption scheme.
-
Galois keys are generated, and a global scale is set, which are configurations related to the encryption and computation processes.
Algorithm 3 details the process of generating the secret and public keys. Within this cryptographic context, the secret key undergoes serialization—a conversion of the object's state into a storable or transferrable format, resulting in a size of approximately 940 kB. Subsequently, the public context is serialized, amounting to 47.3 MB.
For subsequent cryptographic operations, such as encryption, the secret context is retrieved from "secret.txt." The facial embeddings are encrypted employing the CKKS [1] encryption scheme, sourced from the 'tenseal' library, and the resultant encrypted vector is assigned to the variable enc_v1.
The encrypted vector enc_v1 is then serialized, facilitating its storage or transmission. This serialized vector is conserved within enc_v1_proto. The size of the serialized, encrypted biometric features is approximately 446 kB.
In the proposed decentralized identity ecosystem, three core entities interact: holder, verifier, and issuer. The Holder, equipped with a Decentralized Key Management System (DKMS), has the autonomy to create a unique DID and manage its corresponding DID document. This document, stored on the blockchain, includes a CID that points to encrypted biometric features held on the IPFS, allowing for off-chain data storage while maintaining on-chain referential integrity. Holders retain granular control over access to this CID-linked information, ensuring privacy and consent in data sharing. Verifiers, such as contactless car-sharing companies, can authenticate the Holder's credentials by resolving the DID to its document and, with permission, access the detailed data via the CID from IPFS. Issuers like the department of motor vehicles are responsible for issuing credentials embedded with CIDs, maintaining the veracity and currentness of credential information, and managing revocation lists or statuses accessible through IPFS. This architecture not only empowers the Holder with control over their identity but also enables the secure, efficient verification of credentials by Verifiers, underpinned by the trustworthiness of the Issuers. Each party client application participating in this system should have following functionality.
-
Manage DID and DID Document: Generate and update their DID and DID document, including updating the CID that points to additional information stored on IPFS.
-
Control Access: Determine which entities have access to the CID and, consequently, to the information on IPFS.
-
Grant and Revoke Permissions: Use access control mechanisms to grant or revoke permission for Verifiers to retrieve the IPFS-stored information via the CID.
-
Share Verifiable Credentials: Provide verifiable credentials, including the relevant CIDs, to Verifiers when needed and consent to access the extended information on IPFS.
-
IPFS Interaction: Upload and manage data on IPFS, ensuring that the CID in the DID document is always current and points to the correct data.
-
Resolve DID to DID Document: Use the DID to access the DID document on the blockchain, retrieving the CID for additional information.
-
Request Access: Request permission from the holder to access the information linked via the CID on IPFS.
-
Retrieve Data from IPFS: Once granted permission, use the CID to retrieve additional information from IPFS needed for verification.
-
Verify Credentials with Extended Data: Verify the Holder's credentials using both the DID document and the additional data retrieved from IPFS, ensuring all provided information is consistent and valid.
-
Enhanced Credential Issuance: When issuing credentials, include a CID that points to additional data on IPFS, if necessary, for the credential's use case.
-
Update CID in DID Document: Provide tools or services to help Holders update the CIDs in their DID documents, ensuring that only current and valid information is linked.
-
Maintain Revocation Lists: Potentially use IPFS to host revocation lists or other credential status information, making it accessible via CIDs in issued credentials.
Upon completion of the aforementioned process, the car-sharing company will be granted access to encrypted biometric features hosted on the IPFS, accessible via links embedded in the smart contract. To compute the Euclidean distance, it is imperative for the car-sharing company to possess two sets of encrypted features. Consequently, the company should deploy specialized kiosks within vehicles to capture images. Users will present their secret key, possibly in the form of a QR code or an alternative mechanism, allowing the kiosk to encrypt the facial features and transmit them to the company's servers for computation. By design, these kiosks are engineered to preclude the retention of any data, ensuring user privacy. Post-process, the encrypted features remain secure for transport.

|
The encrypted vectors are converted into lazy CKKS vectors, priming them for homomorphic operations sans immediate decryption. These vectors are associated with a cryptographic context vital for computational tasks on en-crypted data, absent of the secret key to maintain security during operations not necessitating decryption. The enc_v1_proto signifies the encrypted facial embeddings. The subsequent step involves aligning the encrypted vector with this context to facilitate computations.
With the encrypted vector duly linked to the cryptographic context, the calculation of the Euclidean distance is feasible, enabling secure and private comparison of biometric data.
The operation commences by computing the discrepancy between two encrypted vectors, enc_v1 and enc_v2. Following this, the dot product of the resultant differential vector with itself is ascertained, yielding the squared Euclidean distance. This value is then encapsulated within the variable euclidean_squared, enabling the quantification of similarity between the biometric features represented by the encrypted vectors, all while ensuring that the data remains encrypted and secure throughout the process.
The encrypted squared Euclidean distance, denoted as euclidean_squared, undergoes serialization to enable its storage and transmission. Without the secret key, decryption attempts by the car-sharing company will be futile, ensuring that computational outcomes remain confidential until the user opts to decrypt them.
Consequently, the car-sharing company is tasked with relaying these computations back to the in-car kiosk. Upon reception, the user, with their secret key, can decrypt the results. The kiosk then determines whether to grant or deny vehicle access based on the decrypted outcome, maintaining a secure and user-controlled access system.
The in-car system initiates by loading the secret cryptographic context and the encrypted squared Euclidean distance. Subsequently, the encrypted value is prepped for decryption by integrating it with the secret context. Once decrypted, the plain squared Euclidean distance is obtained. The in-car system then adjudicates: a value below 100 signifies recognition of the individual, granting access; a value at or above 100 denotes a non-match, thus access is denied. This procedure upholds the integrity of personal biometric data, allowing only the user to decrypt and evaluate the comparison outcome.
This report presents a comprehensive evaluation of an authentication system based on various metrics and processing times of image comparisons. The evaluation metrics include the false acceptance rate (FAR), false rejection rate (FRR), acceptance rate (AR), and rejection rate (RR). Additionally, the report analyzes the average processing times involved in each step of the image comparison process.
The evaluation metrics are calculated based on the number of true positives (TP), true negatives (TN), false positives (FP), and false negatives (FN) observed during the authentication process. Fig.6 shows the system evaluation metrics, where the formulas for the metrics are as follows:
In the examination of system efficiency, a detailed temporal analysis was conducted for each discrete stage of the image comparison workflow. The constituent processes scrutinized were the feature extraction, the encryption of these features, the computation of the Euclidean distance in an encrypted form, and the final decryption and result determination. Fig. 7 shows the time per two image execution. For each of these operations, the average time required was meticulously recorded, facilitating a comprehensive understanding of the time allocation across the entire procedure. These averages were then aggregated to determine the total average duration necessary to complete a single image comparison. The average time per step with average total final time can be seen in Fig. 8. The findings from this temporal evaluation are meticulously tabulated, providing insights into the performance and scalability of the system, and are expounded upon in the ensuing discussion.
In the analysis of the facial recognition system's performance across various thresholds of Euclidean distance, four key metrics were evaluated: false acceptance rate (FAR), false rejection rate (FRR), acceptance rate (AR), and rejection rate (RR). Fig. 9 illustrates how these metrics vary as the threshold level changes and values are displayed in the Table 3. As observed, with increasing thresholds, FAR generally tends to decrease, indicating fewer instances where the system incorrectly accepts a non-face as a face. Conversely, FRR typically increases with higher thresholds, reflecting more instances of the system failing to recognize a true face. The acceptance rate (AR), representing the proportion of true faces correctly identified, tends to increase with lower thresholds. In contrast, the rejection rate (RR), depicting the proportion of non-faces correctly rejected, usually decreases as the threshold is lowered.
The Fig. 10 focuses on determining the equal error rate (EER) of the system, a crucial metric in biometric systems, representing the point where FAR and FRR are equal. This balance point is vital in evaluating the overall reliability and accuracy of the system. The EER was computed by identifying the threshold at which the absolute difference between FAR and FRR was minimal. In this analysis, the EER was found to be approximately 13.93% at a threshold of 160. This value indicates the system’s trade-off point, where both types of errors (accepting false positives and rejecting true positives) are equally probable. The lower the EER, the higher the accuracy of the system. Thus, in this context, an EER of 13.93% suggests a moderate level of accuracy for the facial recognition system under evaluation, highlighting a significant consideration for practical applications and further optimization.
In Table 4, we present a comprehensive comparison of our proposed system with key related works in the field. This comparison focuses on several vital parameters that are pivotal in assessing the sophistication and robustness of contemporary biometric systems.
| Key parameters | [24] | [25] | [26] | [27] | [29] | This work |
|---|---|---|---|---|---|---|
| Homomorphic encryption | ✔ | ✔ | ✔ | ✔ | ❌ | ✔ |
| Decentralized approach | ❌ | ❌ | ❌ | ❌ | ❌ | ✔ |
| AI-driven verification | ❌ | ❌ | ❌ | ❌ | ✔ | ✔ |
| User-centric management | ❌ | ❌ | ❌ | ❌ | ❌ | ✔ |
| Off-chain data storage | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| Temporary access facilitation | ❌ | ❌ | ❌ | ❌ | ❌ | ✔ |
| Protection against adversary attacks | ✔ | ❌ | ❌ | ❌ | ❌ | ✔ |
Firstly, the aspect of HE, a critical component for ensuring data privacy and security, is universally adopted across all the compared systems, including ours. This approach is evident in the works of Sperling et al. [24], Gomez Barrero et al. [25], Yasuda et al. [26], and Alberto Torres et al.[27] , underscoring its significance in the field.
A significant distinction arises in the decentralized approach parameter. Our system uniquely integrates a decentralized framework, enhancing data integrity and reducing reliance on centralized data control, setting it apart from the approaches taken by other related works. This decentralization not only bolsters security but also aligns with modern trends in data management and privacy [28]. In the realm of AI-driven verification, our system stands out by leveraging advanced artificial intelligence algorithms for verification processes, a feature not presented in the referenced works. This integration signifies a leap forward in verification accuracy and efficiency. On the other hand, the work from [29] presents an innovative approach to anti-theft solutions for vehicles. While our methodology addresses a similar challenge, it offers distinct advantages in terms of applicability across different industries where user verification is crucial. A key feature of our solution is that it does not require data storage within the vehicle, allowing for greater flexibility and adaptability. Additionally, while [29] highlights the challenges facial recognition technology faces, such as varying lighting conditions, angles, and other environmental factors, we contend that physiological biometrics offer a more reliable and immutable form of identification. These biometric markers are inherently more difficult to replicate or bypass compared to behavioral patterns, which can exhibit a significant degree of similarity among different individuals. This underscores the potential for error in systems relying solely on behavioral data, further emphasizing the robustness of physiological biometrics as a security measure.
User-centric Management, which empowers users with greater control over their biometric data, is another unique feature of our system, distinguishing it from the other cited works. This approach aligns with the growing emphasis on user privacy and autonomy in data management. Regarding Off-chain Data Storage, all the systems under comparison, including ours, employ this method. This is indicative of a shared recognition of the importance of secure and efficient data storage solutions outside the blockchain. Our system also uniquely facilitates Temporary Access, a feature not seen in the other works. This adds a layer of flexibility and user control, especially useful in scenarios requiring time-bound access permissions. Finally, in terms of Protection Against Adversary Attacks, our system, along with the system proposed by Sperling et al., demonstrates robust mechanisms to safeguard against various cyber threats, an aspect where some of the other compared systems fall short. Overall, this comparative analysis underscores the advanced features and enhanced security measures of our proposed system, setting it apart from existing works in significant ways.
In comparing our system's performance with that of Alberto Torres et al. [27], a substantial enhancement in pro-cessing time is evident. Our system demonstrates an impressive average time of only 1.4 seconds per image pair comparison. This duration encompasses the entire gamut of operations, including key generation, encryption, decryption, and Euclidean distance calculation. In contrast, the system evaluated by Alberto Torres et al. [27] required 10.4 minutes for each comparison of two biometric templates in an encrypted domain. This marked reduction in processing time represents a significant advancement in the efficiency of biometric systems. However, it is crucial to acknowledge that the computations in our study were conducted on a different biometric template. This distinction is important as it might influence the direct comparability of the two systems' performance metrics. Nevertheless, the improvement in processing speed in our system is a noteworthy achievement in the realm of biometric template comparison, potentially contributing to more efficient and practical applications in the field.
Our research methodology is focused primarily on the mechanisms of authentication and verification, without delving into the intricacies of the car rental process itself or the operational aspects of in-car hardware. It's important to clarify several key aspects of our approach to ensure a comprehensive understanding:
-
Verification Image Deletion: Our approach mandates that images used for verification purposes be deleted by the car sharing company's hardware immediately after the process is completed. This step is crucial in mitigating risks associated with the unauthorized access to or misuse of biometric data.
-
Biometric Data Privacy: The privacy of biometric features is a foundation of our methodology. By storing the private key exclusively on the user's device, we ensure that biometric data remains inaccessible to any third party, including the car rental company. This design principle safeguards users' biometric information against external breaches or internal misuse.
-
Limited Data Disclosure: The car sharing application is designed to only communicate a boolean value indicating the success or failure of the verification process. This minimal data exchange ensures that sensitive information, such as the user's biometric data or the specifics of their verification, remains confidential.
-
Homomorphic Encryption: We employ homomorphic encryption specifically to preserve the privacy of biometric features. This advanced cryptographic technique ensures that even the result of the Euclidean distance calculation, used in the verification process, is disclosed only upon successful private key verification. Essentially, this method enables the secure processing of encrypted data, thereby ensuring that sensitive information remains private and inaccessible throughout the process.
V. CONCLUSION
The proposed decentralized biometric authentication system for car-sharing applications has potential positive impacts on privacy, security, convenience, and personal data control. Utilizing advanced cryptographic techniques, AI-driven biometric verification, and a user-centric design, the system aims to enhance security, streamline identity verification, comply with data protection regulations, and promote fairness. In the context of car-sharing, the approach is expected to improve security, user experience, competitiveness, regulatory compliance, scalability, interoperability, and corporate social responsibility. Additionally, the system could have significant implications for governments, impacting regulatory compliance, public trust, infrastructure, policy development, national security, and sustainable transportation. The research concludes by presenting a novel decentralized biometric authentication system, highlighting its accuracy, reliability, usability, scalability, and GDPR compliance. Future research can explore additional biometric modalities, advanced security measures, alternative storage and access control mechanisms, and improved interoperability to further enhance the performance and applicability of the system. By continuously refining and adapting the system, we can contribute to the development of a more secure, privacy-preserving, and user-centric authentication landscape for contactless car-sharing and other industries. Additionally, the data security and integrity protocols of car sharing companies need to be considered. There are privacy concerns regarding the data stored in the vehicle's black box camera and GPS device, particularly concerning car companies' access to information about lessees' locations, thus, renders them hesitant to utilize the car-sharing system, as it equates to sharing their data without their explicit knowledge.